Posts Tagged MAC
Authentication Primitives for Memory Authentication
Posted by protogenist in Application Development on September 3, 2012
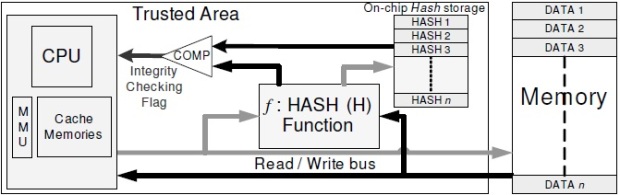
Hash Functions. The first strategy (Figure 1.a) allowing to perform memory authentication
consists in storing on-chip a hash value for each memory block stored off-chip
(write operations). The integrity checking is done on read operations by re-computing
a hash over the loaded block and by then comparing the resulting hash with the on-chip
hash fingerprinting the off-chip memory location. The on-chip hash is stored on the
tamper-resistant area, i.e., the processor chip and is thus inaccessible to adversaries.
Therefore, spoofing, splicing and replay are detected if a mismatch occurs in the hash
comparison. However, this solution has an unaffordable on-chip memory cost: by considering
the common strategy of computing a fingerprint per cache line and
assuming 128-bit hashes and 512-bit cache lines, the overhead is of 25% of the memory
space to protect.
Figure 1.a Hash functions: Hashn = H(DATA n)
MAC Functions. In the second approach (Figure 3.3-b), the authentication engine
embedded on-chip computes a MAC for every data block it writes in the physical memory.
The key used in the MAC computation is securely stored on the trusted processor
chip such that only the on-chip authentication engine itself is able to compute valid
MACs. As a result, the MACs can be stored in untrusted memory because the attacker
is unable to compute a valid MAC over a corrupted data block. In addition to the data
contained by the block, the pre-image of the MAC function contains a nonce. This
allows protection against splicing and replay attacks. The nonce precludes an attacker
from passing a data block at address A, along with the associated MAC, as a valid (data
block, MAC) pair for address B, where A 6= B. It also prevents the replay of a (data
block, MAC) pair by distinguishing two pairs related to the same address, but written in
memory at different points in time. On read operations, the processor loads the data to
read and its corresponding MAC from physical memory. It checks the integrity of the
loaded block by first re-computing a MAC over this block and a copy of the nonce used
on write operation and by then comparing the result with the fetched MAC. However,
to assure the resistance to replay and splicing, the nonce used for MAC re-computation
must be genuine. A naive solution to assure this requirement is to store them on the
trusted and tamper-evident area, the processor chip. The related on-chip memory overhead
is 12.5% if we consider computing a MAC per 512-bit cache line and that we use
64-bit nonces.
Figure 1.b MAC functions: MACn = MACk(DATA n)